Cisco ACI means Application Centric Infrastructure
Why application designers and developers don't want to speak to network engineers.
In my previous life I was an enterprise architect and I led design and development of software systems in many projects. When we were in the phase of planning the procurement and the setup of the various environments for the project (dev, test, QA, prod) I was bored by the meetings with the infrastructure guys.
What I needed was a given amount of memory and CPU power, that I could calculate myself, on a single big server or on a number of smaller machines. Then I needed connectivity among the different deployment units in my architecture (a cluster of web servers, a cluster of application servers, a database and some pre-existing systems), and just some services like load balancing.
But those nasty network engineers and the ugly security guys wanted to discuss a long list of requirements and settings: vlans, ip addresses, subnets, firewalls, quality of service, access lists :-(
I was only interested in application tiers and dependencies, SLA, application performances and compliance and I wanted to discuss that in my language, not in their unfamiliar slang.
How the system engineers see the world: a number of devices with their configuration.
How I see the world: a number of servers (or processes) with their role in the application. We can call them End Points.
The communication can be described as a contract.
Provided by some end points, consumed by others.
And saved as a reusable policy, that could be applied to End Point Groups:
Eventually, network services like load balancers or firewalls can be added (creating a service graph):
You can easily understand that our meetings were not that easy ;-)
It was not their fault (and of course it was not... mine): we only saw the world from different angles, or maybe with different glasses.
For the software guys, abstracting the topology of the deployment is essential. For the system guys, devil is in the detail and they need to know exactly what traffic is flowing to engineer the setup accordingly.
Having a set of policies that describe the desired behavior makes the conversation easy: what service is offered by a end point group, what group (or single end point) can consume it, what SLA should be enforced, etc... Contracts could be: access to a web application on http on port 80, access to montoring agents or to log collectors, access to a LDAP server for authentication and so on.
You will see later in the post that ACI allows this conversation.
After long discussions and escalations, the setup of the environment was never as fast as I needed.
It was not the DevOps time yet, but we still tried to roll out many builds of the application for rapid prototyping and quick wins.
Now imagine that you were able to agree on the policy definition.
Having an instant enforcement of those policies on all your network devices without touching them one by one, in a consistent way that prevents human errors and grants compliance by default, and have it done soon would be a miracle... or a magic.
Now we have a network architecture that makes this miracle real: Cisco ACI.
A single software controller (redundant, of course) manages all the network connectivity, security and the network services like load balancers and firewalls.
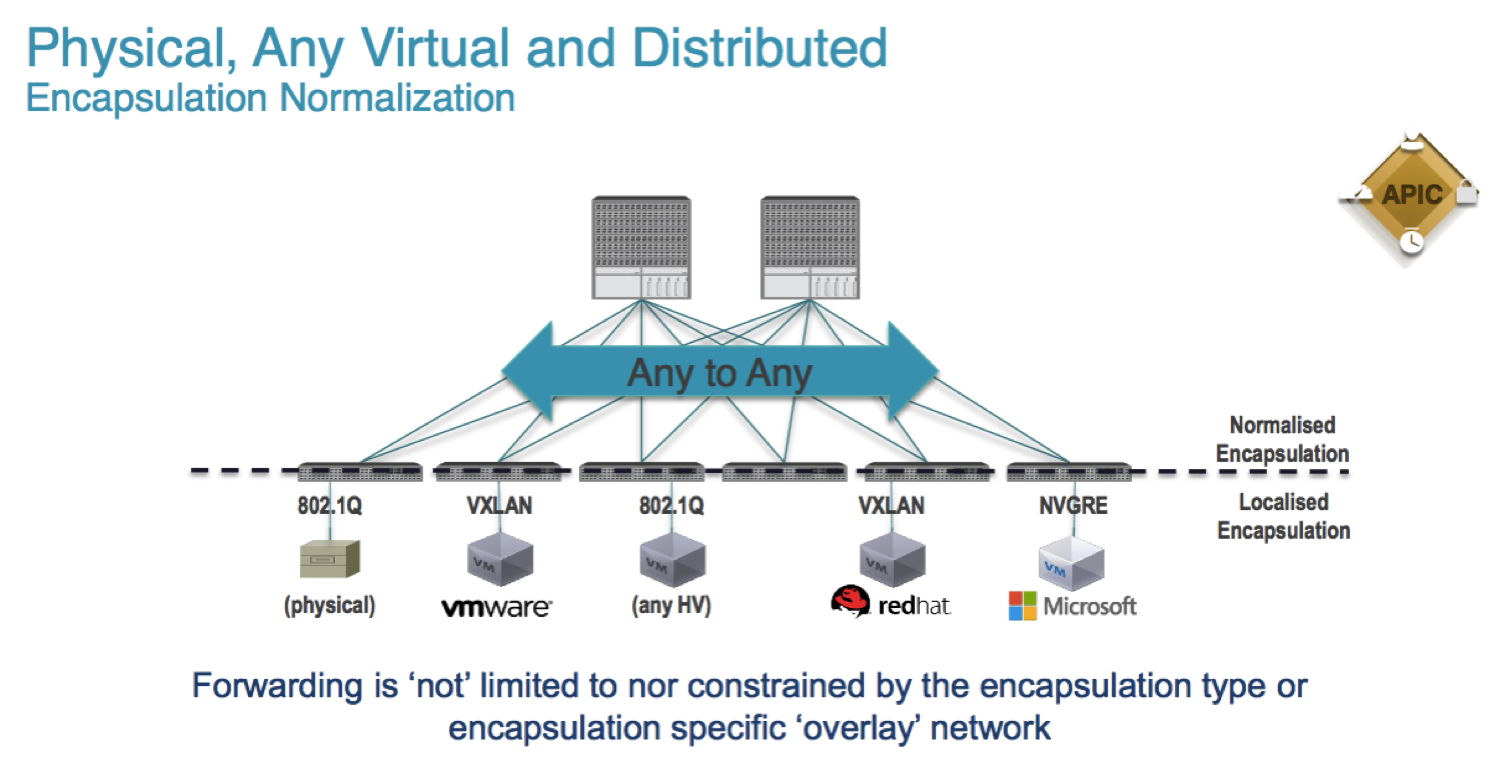
The network is a hardware fabric, with great performances, scalability, resiliency that I will not discuss here (see the links below for the detail), that extends smoothly into the virtual networks of any vendor or open source solution enforcing the policies for physical servers and VM as end points without any difference.
The controller (named APIC) has a GUI but, most important, a rich set of open API that can be invoked by your scripts, by orchestration tools from Cisco or 3rd parties, by cloud management systems.
You can create the policy from here, and also see the "telemetry" of the network with easy display of the health score of the fabric or individual applications as well.
Use cases for ACI
Fast provisioning
A stateless network like ACI can be provisioned and completely reshaped in seconds by pushing new policies through the controller.This concept is pretty similar to what the UCS Service Profile made possible in the server industry, introducing the stateless computing.
You can add the complete configuration for a new application to a multitenant shared infrastructure, you can create a new tenant environment, you can create the test environment and the production environment just by cloning the development environment and applying any needed policies to ensure compliance.
Everything is represented as a XML document or a JSON data structure: in any case a small piece of text data that can be saved, versioned and built automatically by a automation script or tool.
Infrastructure as code is one of the pillars of DevOps.
Physical and virtual networking managed the same
When you design End Point Groups and their Contracts, they can be mapped to physical servers (i.e. servers running a single Operating System, like Linux, Unix or Windows servers) or to VM running on any hypervisor.Traffic from a VM is encapsulated and isolated from other VM's, then the policies are applied to allow it to flow to the destination (physical or virtual).
The spine-leaf architecture of the fabric is extended by a virtual leaf that runs in the hypervisor, under the control of the APIC Controller.
Service Graph
The integration of network services (LB, FW, etc.) from 3rd parties is easy thanks to the Opflex protocol, that allows the extension of the declarative style (vs imperative) of the configuration.You can add the services to a contract and all the end point that offer and consume that contract will benefit from the insertion without any need for local configuration (e.g. changing the default gateway to the newly inserted firewall).
Many 3rd party vendors added - or will add soon - Opflex agents to their product. The wide ecosystem of ACI becomes richer every day.
Easy deprovisioning
Often, when an existing application is deprovisioned, the network and security configurations created for it are not deleted.This is due to different reasons: either because it's hard to find them (not all the organizations use a CMDB to track everything) or because the responsible for the operation is afraid of removing firewall rules, ACL, vlans that could potentially be used by a different application, creating a problem as a consequence.
If you have all the policies for a given application defined as attributes of a specific Application Network Profile in APIC, simply removing that ANP will clean all the configurations. You were not applying rules to ports (where other application could be attached) but to end points.
Finally, what advantages can you get from ACI?
Centralized Policy-Defined Automation Management
• Holistic application-based solution that delivers flexibility and automation for agile IT
• Automatic fabric deployment and configuration with single point of management
• Automation of repetitive tasks, reducing configuration errors
Open and Comprehensive End-to-End Security
• Open APIs, open standards, and open source elements that enable software flexibility for DevOps teams, and firewall and application delivery controller (ADC) ecosystem partner integration
• Automatic capture of all configuration changes integrated with existing audit and compliance tracking solutions
• Detailed role-based access control (RBAC) with fine-grained fabric segmentation
Real-Time Visibility and Application Health Score
• Centralized real-time health monitoring of physical and virtual networks
• Instant visibility into application performance combined with intelligent placement decisions
• Faster troubleshooting for day-2 operation
Application Agility
• Management of application lifecycle from development, to deployment, to decommissioning in minutes
• Automatic application deployment and faster provisioning based on predefined profiles
• Continuous and rapid delivery of virtualized and distributed applications
If you liked this post, you may want to read also ACI for (smarter) Simple Minds. You have passed the basic stage now :-)
Links
Serious product documentation
ACI Marketing pageACI at a glance
ACI in one page
Application Centric Infrastructure (ACI) Documentation
Learning ACI - Adam's blog








No comments:
Post a Comment